What is forensic recovery and logs?
The main principle of forensic recovery is repeatability. The GPR (GoPro Recovery) software works to conform with standard rules. The other very important aspect is that nothing is ever changed. Part of the forensic option with GPR is additional information in the logs, this includes GPS, HASH value and directory runs.
A very important part of GPR software is the log. All versions of the software see the basic features, but for forensic opertion there are two very important additions - fragments and MD5 hash values.
Fragments
A typical GoPro, or DJI video will be saved in often a few hundred fragments. By clicking on the frgament column in the log, the forensic version of the software will display all fragment locations. This means that if it was required, a third party could take the same basic chip image and generate the same video file using the information in the log.

This extract from the log shows file names, and also the fragment count.
When the frgament count is clicked on with the mouse (in the Forensic version,) this is expanded to give each fragment detail - as below
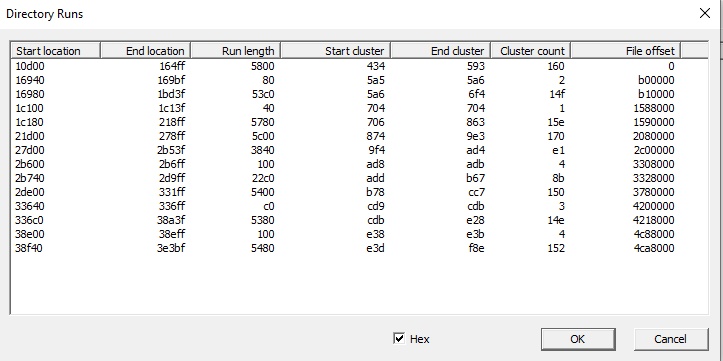
In the example above we can see the sectors that each fragment is found, and the length, in sectors, or clusters of the fragment.
GPS Locations
Some cameras, including Hero 7 to 11 contain GPS detectors. GPR will extract these values and in the forensic version of the software, will store the location in the log. The location stored is the first one found in the video. The GoPro Hero GPS will not always register it's location when in doors.
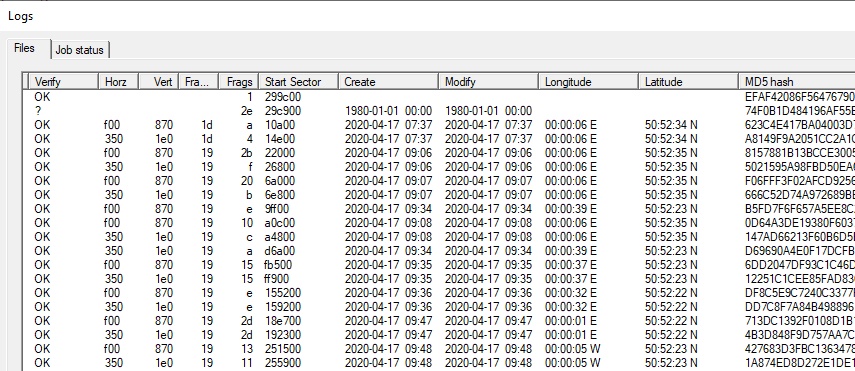
You may note in the above example that camera moved from the Eastern hemisphere to the West. CnW is based in a town on the Greenwich Meridian
Accelerometer information.
Most recent GoPro cameras do record accelerometer and gyroscope data. On the forensic version, when the file is recontructed from fragments this information is now included, from V2.97 onwards. It can be vewed with a free program
https://goprotelemetryextractor.com/free/#
Hashing
With the forensic option, every file is hashed with an MD5 hash. An MD5 hash value that is in effect unique for a specific file. If even a single bit is changed, the hash value will be totally different. The advantage of this is if a file is transmitted, or copied anywhere, as long as the hash value is the same, then we know the file has not been changed on transmission. Also, for evidence, it means that the file has not been edited or changed in anyway. The Hash value is a 16 byte number, normally displayed as a Hex string. (The screen shot above has been cropped so only the start of the hash value is displayed).
E01 files
Many forensic investigations start by imaging a device and creating an .E01 file. This is a compressed file, but also has many security features built in. In effect, it is not possible to tamper with the data within the file. The forensic version of GPR will read these files in the same way as a normal image file.
GPS Locations
Some cameras, including Hero 7 to 11 contain GPS detectors. GPR will extract these values and in the forensic version of the software, will store the location in the log. The location stored is the first one found in the video. The GoPro Hero GPS will not always register it's location when in doors.

You may note in the above example that camera moved from the Eastern hemisphere to the West. CnW is based in a town on the Greenwich Meridian
Accelerometer information.
Most recent GoPro cameras do record accelerometer and gyroscope data. On the forensic version, when the file is recontructed from fragments this information is now included, from V2.97 onwards. It can be vewed with a free program
https://goprotelemetryextractor.com/free/#
Hashing
With the forensic option, every file is hashed with an MD5 hash. An MD5 hash value that is in effect unique for a specific file. If even a single bit is changed, the hash value will be totally different. The advantage of this is if a file is transmitted, or copied anywhere, as long as the hash value is the same, then we know the file has not been changed on transmission. Also, for evidence, it means that the file has not been edited or changed in anyway. The Hash value is a 16 byte number, normally displayed as a Hex string. (The screen shot above has been cropped so only the start of the hash value is displayed).
E01 files
Many forensic investigations start by imaging a device and creating an .E01 file. This is a compressed file, but also has many security features built in. In effect, it is not possible to tamper with the data within the file. The forensic version of GPR will read these files in the same way as a normal image file.